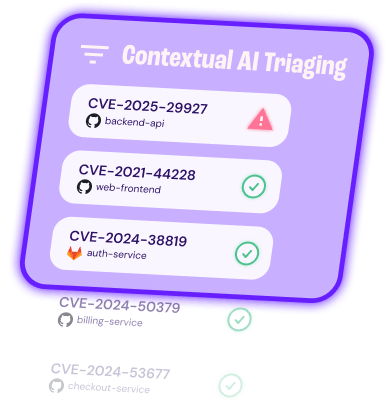
Triage You Can Trust

Cut through the noise with evidence-backed triage
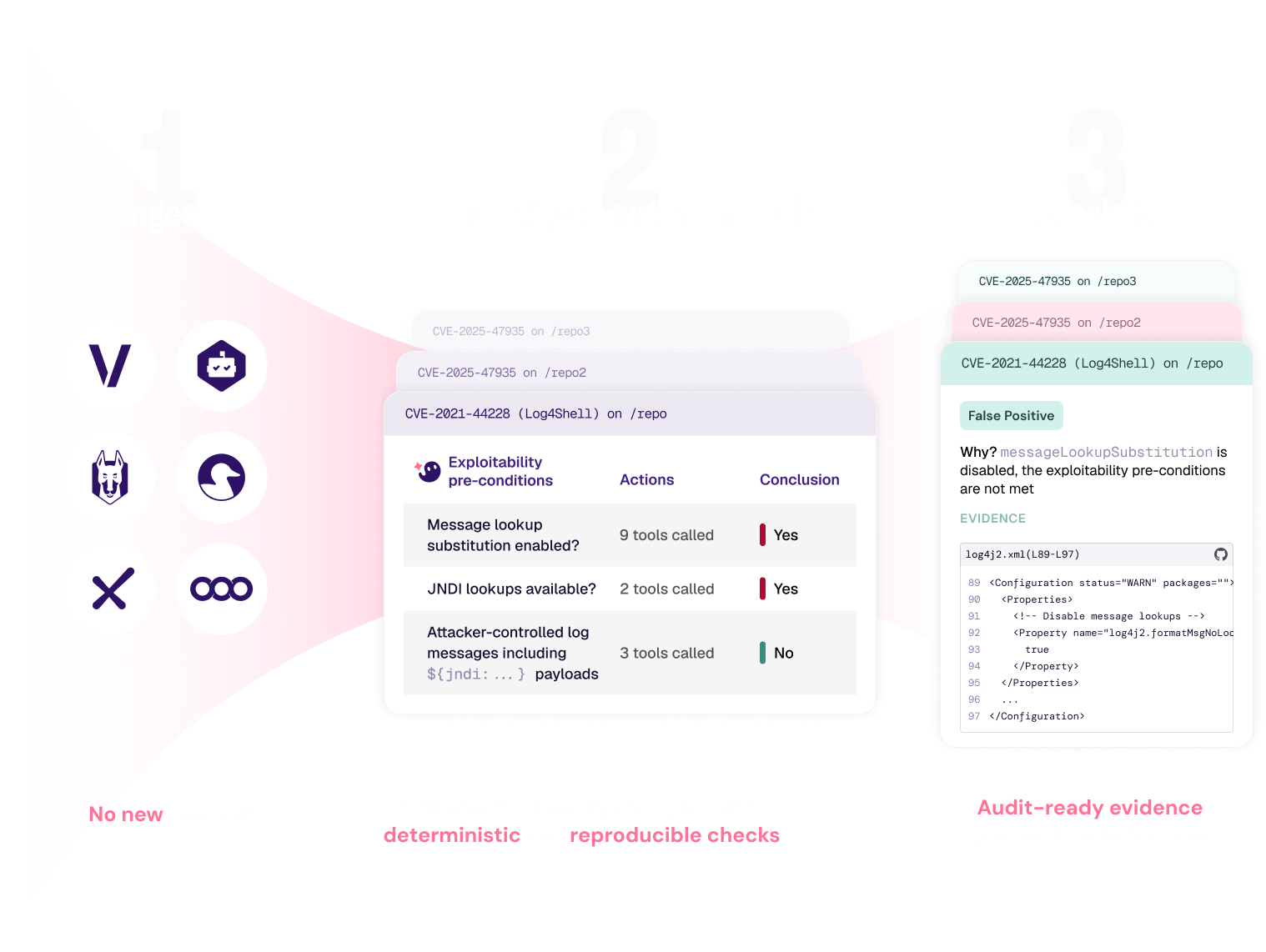
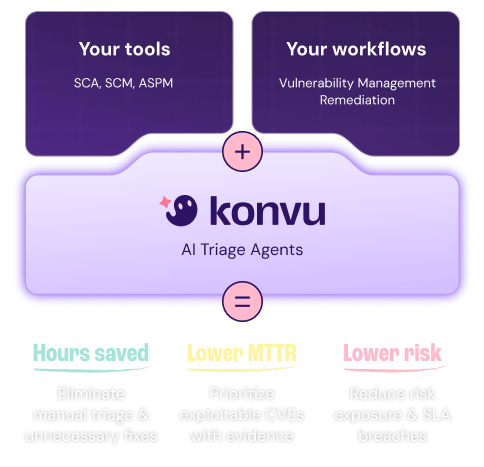
Konvu closes the gap between AppSec and devs, combining security insights with code and optional runtime context to deliver automated, evidence-backed triage.
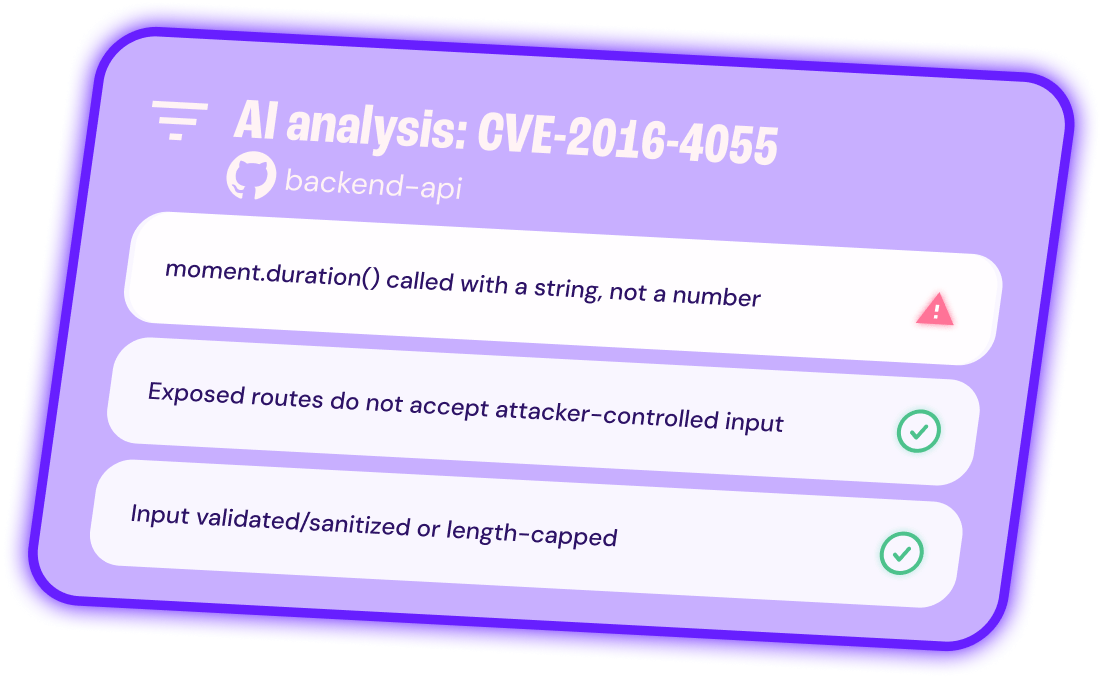
Say goodbye to false positives
Dismiss non-exploitable vulnerabilities with decisions backed by reasoned analysis and evidence your security and dev teams can trust.
- Cut backlog and noise by ignoring non-exploitable findings with confidence.
- Trust every decision with documented investigations, code-level and optional runtime evidence.
- Stay in control with policy-based confidence thresholds and human-in-the-loop reviews.
Zero in on exploitable vulnerabilities
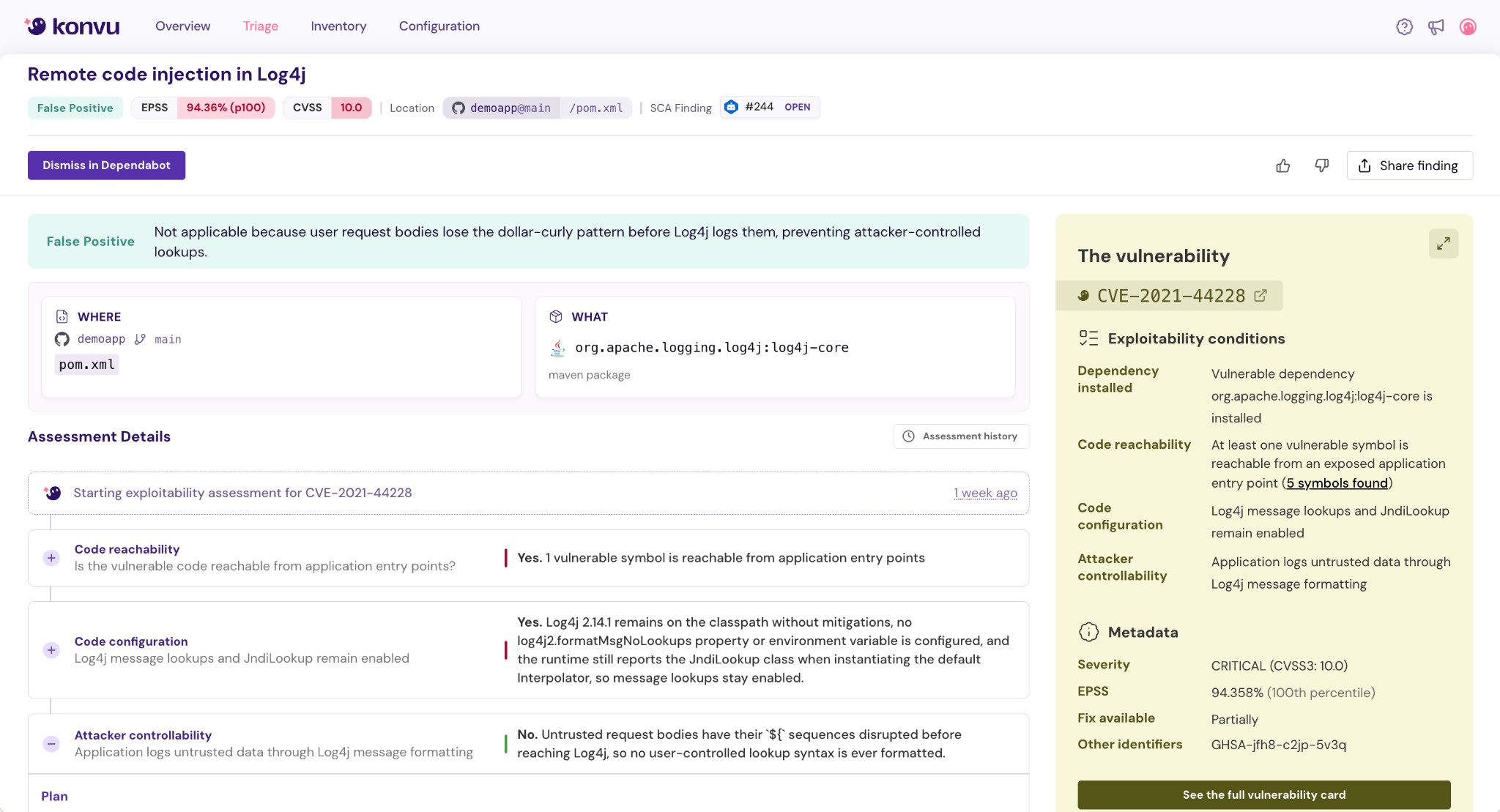
Surface the few CVEs that are actually exploitable so teams act fast and meet SLAs.
- Check exploit conditions against Konvu's vulnerability database enriched with exploitability conditions and affected functions.
- Confirm exploitability with evidence beyond reachability by running deterministic checks on code paths, configs, data flows and optional runtime signals.
- Prioritize vulnerabilities based on Known Exploited Vulnerability (KEV), exploit availability, and Exploit Prediction Scoring System (EPSS).
Built for your workflow
Keep your scanners and process. Konvu installs quickly and pushes decisions where work already happens.
- Install in minutes with lightweight setup that supports your languages and technologies.
- Keep your scanners and avoid rip-and-replace or partial coverage from a new tool.
- No new dashboards: decisions sync into your tools so teams keep their process.
Average noise reduction
Fortune 500 Retail
Security Lead
Konvu gave us clarity. It dismissed the non exploitable findings and put the real risks at the top of the list.
Faster MTTR on real issues
B2B SaaS Company
Chief Technology Officer
My team was spending 15+ hours every week fixing false positives. Now we save all that time for real security work.
Case study coming soon →
Learn how a retail giant with 80k+ employees transformed their vulnerability management by automatically triaging Black Duck Polaris findings with AI-powered evidence.
Read case study →Built for enterprises
Secure and reliable so every security and engineering team can trust and adopt. Enterprise-grade from day one.
SOC 2 Type II Certified
Independently audited and certified for security, availability, and confidentiality controls.
Privacy Mode Guarantee
We never store your code and ensure your code data is never stored by model providers or used for training.
Global Governance
Full control over authentication and user provisioning with SAML SSO, SCIM, and RBAC.